What does a read-only file mean. file attributes. With the possibility of specifying an absolute position
File Attributes
Each file has a number of characteristic properties - attributes. The most important file attributes are: name, extension, length, time and date of creation. File name. The name, or file name, just like the name of a person, the name of a document, a book, serves to be able to distinguish one file from another, to point to the desired file.
How to select a command to execute on double click?
Unfortunately, this dialog is the same one that contains security information on a different tab. Here is one way to solve the problem. This ensures that all files and directories created in the directory tree will be owned by the current user and will be owned by the group that owns the directory in which it is created. Navigate to the top of the shared folder. . There is a workaround to resolve the permissions issue. This ensures that all files are created with the group that owns the directory.
File extension. In addition to the name, each file may or may not have an extension. The extension is used to characterize the contents of a file in a certain way. For example, the doc and txt extensions indicate that the file contains some document or text, and bmp extension has a file containing an image in bitmap format. The extension, if any, is separated from the file name by a dot. V operating system MS DOS extension can contain from one to three characters, for example, otchet4.doc, vedzarpl.txt, picture.bmp, and in Unix systems and Windows 9.x allowed more than three characters. If there is no extension, then the dot is not put in the file name. The name together with the extension is called the full name of the file. File length. The next important attribute of a file is its length. The length of a file is equal to the amount of space the file occupies on the disk or tape, and is therefore measured in bytes. The value of this attribute is used to determine whether a file can be placed on a free area of a disk drive and for some other purposes. Time and date the file was created. When a file is first written to disk, or when changes are made to a file using the system clock ( special program, which is part of the operating system), the time and date of writing the file to the disk device are automatically recorded. When the computer is turned off, the system clock is maintained by special batteries or other power sources.
What does the Hidden attribute mean?
Yes, you can just pass the number back to the file attributes -transfer, but displaying the symbolic format to the user will be more useful at times. Symbolic links: file attributes returns the attributes of the link's target. This will crash if the symbolic link is hanging. So, what needs to be done in order for this information to be established? Classically, one would simply start a remote shell on the server and send the correct commands to it. Metadata allows users and applications to define and store user data associated with their files in a field.
v MS DOS operating system files have four more attributes - read-only, system, hidden and archive. Each of these attributes has exactly two states - the attribute is enabled or the attribute is disabled. Enabling a read-only attribute(sometimes called the access control attribute) means that the file is not available for making any changes to it. In addition, the destruction of such a file is complicated. After turning off the read-only attribute, the file is available for any operations. System attribute usually only enabled for core operating system files. For all other files, the system attribute, as a rule, is turned off. Attribute hidden d is enabled for those files that, when viewing the list of files located on the disk device, are not included in this list by the operating system command. Other files have the value of the hidden attribute turned off. To ensure the reliability of information storage on disk devices, it is necessary to have one or two copies of files containing important information. To do this, organize archive files. When a file is written to an archive, the archive attribute is enabled. This means that a copy of the latest version of the file is in the archive. If you make any changes to such a file, the archive attribute is turned off. This means that the archive contains an outdated version of the file (or the file was not archived at all). Special programs-archivers, keeping track of the value of the archive attribute, can update the archive only those files in which changes have been made. This allows you to optimize the work of archivers.
In the Insert box, hover over a single file or folder with your mouse. If the element looks like this, you are in the right place. If the item does not look like the image above, please select one of the links below. The main way to use metadata is to create metadata templates. Templates are a logical grouping of metadata attributes that help classify content. For example, a marketing team in a retail organization might have a brand template that defines a piece of content in more detail.
File management.
File management in Windows XP is carried out using the Explorer program or the My Computer folder and is reduced to the following operations:
- copying, moving and deleting files (not covered in this course);
- setting standard attributes;
- setting additional attributes;
- assignment of permissions.
All these operations are available through the item Properties context menu called for a file, folder, or any combination of them. Depending on which object the right mouse button was pressed on, the properties window will contain a different number of tabs.
Each of these attributes can also add data entry restrictions. When it comes to metadata, templates are important for several reasons. Ensuring consistency in your enterprise metadata To reduce errors and speed up data entry by employees or team members To enable advanced search queries. When using a metadata service, it is important to consider which functional groups will benefit from adding and supporting metadata templates. Our suggestion is to consider using metadata in the following areas.
Click right click mice in an empty space working area explorer window calls context menu for the parent object. Thus, clicking on an empty space within a folder will bring up that folder's context menu, and clicking on an empty space while browsing the contents of a drive's root folder will bring up the drive's context menu.
From custom terms of service to purchase contracts, metadata attributes such as subscription date or contract term can be useful to discover. Supplier Management - On board and manage contracts and supplier details for easier reporting and expense management. Help sales representatives find important collateral. Marketing. Digital asset management and sales. Centralize multiple digital asset repositories to make branding easier. Project management - adding structure and status to documents. Use metadata to find common forms for analyzing employee data.
- Legal - Classification of legal contracts.
- Sales.
- Organize content by product line, use case, or sales geography.
Set default file and folder attributes.
The standard file and folder attributes are an obsolete primitive means of controlling access to files and folders. In Windows XP and other modern operating systems, there are much more flexible and convenient mechanisms for managing files.
Standard attributes of files and folders are set on the General tab of the properties window. The appearance of this tab for files and folders is largely identical:
After adding a template to the right pane, you can set or select values for the pre-selected attributes. Note. You can assign up to 100 metadata templates to a specific file or folder. You can also add additional attributes for a specific file. After adding this attribute to the right pane, you can set a custom value in the field.
Using advanced search with metadata templates
These additional attributes do not propagate to other files. If you perform a search, it will process metadata values in the same way that filenames or file text are processed. You can also use advanced search to filter results on specific metadata templates. To do this, enter search query in the search bar and search. A set of filter options will appear next to the search results, and you can use the Metadata drop-down menu to select a specific metadata template.
Folder properties
File Properties
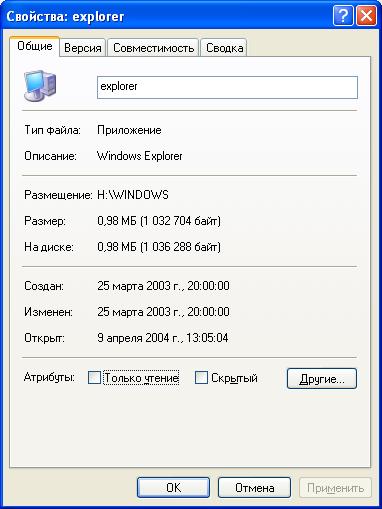
On the General tab, you can find out:
- the actual and occupied size of the file or folder on the disk;
- number of files and subfolders (for a folder);
- date and time of creation, date and time of last modification and opening (for a file).
In addition, the checkboxes on this tab set the two standard attributes Read Only and Hidden. In general, Windows XP, like any other Microsoft operating system, supports four standard attributes for files and folders located on the FAT, FAT32 and NTFS file systems.
How do I add templates to my business?
Once you have selected a template, you can use the attribute categories for that template to filter your search results. A few things to consider when creating templates. Once a template is published, the following elements cannot be changed: Attribute type Edit, rename, or remove selection options.
- Templates can have a maximum of 125 attributes and 128 select list items.
- Template attributes can only be text, numbers, dates, or picklists.
Attribute | Description |
Archival | Indicates that the file has been modified since it was last archived, or Reserve copy. This attribute is set by most programs when a file is created or modified. This attribute is reset by archivers and backup utilities. Helps archivers and backup utilities to detect changed files. How does metadata work with external collaborators in a folder?Yes, you can use metadata without templates. Read and write access to existing templates will match default settings related folders. New templates can only be added by users within the enterprise; external employees outside the enterprise will not be able to add new templates. How does metadata work with folder permissions?The metadata will adhere to folder-level permissions. A collaborator with view item permissions can view metadata, and a collaborator with download permissions can edit metadata values. For example, if the collaborator is a folder viewer, that person will be able to view the metadata and not edit it. If the collaborator is the uploader preview in the folder, that person can view and edit the metadata. |
Only for reading | Indicates that the file cannot be modified. Setting this attribute cannot serve to restrict access to a file or folder, but is intended to avoid accidental overwriting or deletion of an object. Most programs, when attempting to write data to such a file or attempting to delete it, ask the user an additional question as to whether they really want to delete the file or folder. Are there any known limitations?How does metadata work with shared links? Metadata doesn't appear in shared links unless the recipient is a collaborator in a folder with parent folders. The metadata will not be removed from the file until the file is deleted or trashed, or if the user removes the metadata directly. Change prohibitionMost programs, when viewing a file marked read-only, will refuse to delete or modify it. Basically, it's like a "more serious" read-only flag, and is mostly handled that way. It's also a "super-hidden" attribute. Even if you enable "Show hidden files”, system files will not be displayed. There can only be files in folders. Through the properties page of a file or folder. |
Specifies that the file or folder is not displayed on the screen when viewed. Designed to hide important system files from the user. Most file programs, including Explorer, have a setting to bypass this attribute. |
|
Systemic | Indicates that the file or folder is a system file. In Windows 2000, it is only used for backward compatibility with MS-DOS, Windows 3.x and Windows 9x. This attribute marks the files used for Windows boot 2000, in the root directory of the system and boot drives. Cannot be changed via graphics windows tools 2000, but can be changed via command line or third party programs. General File AttributesIt doesn't mean read-only or not read-only. To set all files in a read-only folder. For multiple files and folders. Various viruses cause different types damage to your computer. There are some viruses that will cause destruction, such as the encryption of recently used files, so from the virus writer. You can still see the files if you specify hidden files and folders and disable operating system hidden files. If the virus is able to restrict folder options, chances are your files have been destroyed by the virus, but in fact they are perfectly safe and have just been hidden on your system. There is still hope if you think your files have disappeared due to a virus. Here's how to check if all the files are still there, and if they are, you can reset the file attributes so they can be viewed normally again. How to show hidden files and folders or system files. |
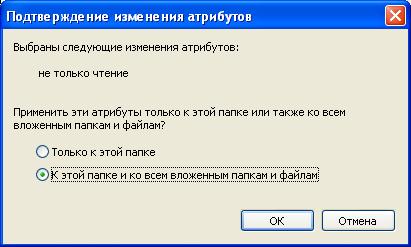
Changing the attributes of files and folders occurs after pressing the OK or Apply button. If you have changed the attributes for a folder, then Windows XP will ask you to clarify whether you need to change the attributes of subfolders or files.
The process of changing attributes is usually quite fast, although it can take a long time if the operation involves several thousand files and folders.
What is a file type?
Go to Control Panel and open Folder Options. Click the View tab and select Show Hidden Files and Folders. Then uncheck "Hide protected operating system files". Please note that some viruses that are still active on the computer will revert the changes you have made. Therefore, first make sure that your computer is free of viruses.
Try to find missing files on your hard drive. There is a tool that can help you find files or folders created or modified in the last 1-3 months. If you managed to find your hidden but visible files, since you've configured the folder options to show them, you need to show hidden files. Here are 4 ways to reset the system and hidden attributes.
Changing Standard Attributes from command line.
To change the standard attributes of files and folders from the command line, use the command attrib
attrib[.exe] [+r|-r] [+a|-a] [+s|-s] [+h|-h] [[drive:][path]filename] ]
Description of attrib command keys:
Key | Description This is an old school technique without using any software. Just launch a command prompt, enter the following command. You can also use the asterisk character to define multiple extensions. This security context, along with the run-time user that this process resides in, will determine that this process is allowed. This is a tangible, real scenario and easy to imagine or even reproduce. Consider the following output. Only the owner has permission to write to the file. When you view the ownership of a file, it should be immediately obvious to users what can and cannot happen to the file. Well, nothing works: root processes can still get into the directory and manipulate it. Other processes will not be able to, as shown in the following attempt to enter this directory. |
[drive:][path]filename What users like you and me do in order to know what is or isn't allowed is to check the actor information, the resource information and then match the permission we want to check against the allowed permissions. We could write access controls for this file like this. It's not so much the content of the rules that we want to clarify, but the way the rules are written. They all contain information such as. A process context that acts on something in the resource context, on which the process acts on the resource type or class, the permission or permissions allowed given the first three informational messages. In other words, you can write it like this. | Specifies the location of the folder and file(s) whose attributes are to be changed. Are wildcard characters allowed? and * |
Sets the processing of eligible files in the specified folder and all subfolders |
|
Specifies that more than just files matching the parameter should be processed. File name, but also folders satisfying the same condition |
To change the attributes of files and folders with the "system" or "hidden" attribute set, you must first remove these attributes.
Setting additional attributes.
In Windows NT, 2000, and later in Windows XP, new attributes were added to the standard attributes of files and folders, called optional. All of these attributes can only be set for files and folders located on NTFS volumes. The FAT and FAT32 file systems do not support additional attributes.
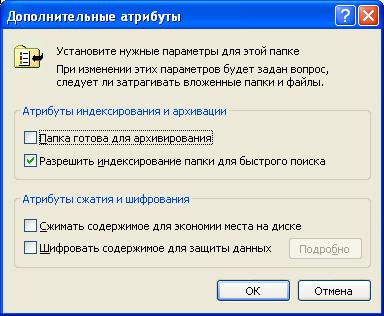
To set additional attributes, in the properties window of a file or folder, click the Other button. This will open the window for setting additional attributes. The view of this window for files and folders is identical:
Additional folder attributes
Additional file attributes
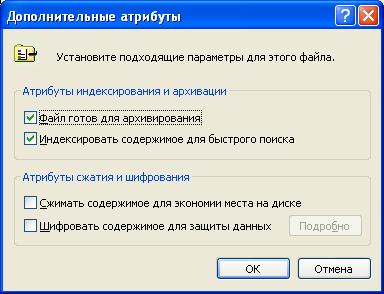
Let's consider additional attributes in more detail.
Attribute | Description |
Indexing files slows down saving and modifying such files quite a lot. The reason for this is the complete re-indexing of the contents of the file each time it changes.
The compression and file encryption attributes are mutually exclusive. In the current version of NTFS, encrypted files cannot be compressed using the operating system.
File encryption.
encrypted file system(Encrypting File System, EFS) supports encryption of files stored on NTFS volumes. Encryption in EFS is based on public key technology and is provided by a service integrated into the system. This allows:
- facilitate the management of encrypted files;
- protect important files from unauthorized access to them by other users and intruders, even if seized hard drive from a computer and connecting it to another computer;
- provide transparent decryption of files when they are accessed by the rightful owner;
- make transparent copying and moving of encrypted files - all file operations are performed without decrypting files;
- store encrypted user data on different computers in local network and in roaming profiles - the user's certificate is stored on the server in the certificate authority, which allows you to use this certificate from any computer in the domain.
A user who has a private key to an encrypted file can open this file and work with it as with a regular document - decryption will be performed automatically by the system. A user who does not have such a key cannot access the file.
When working with encrypted files, Windows XP maintains security at the proper level. This means that all working copies of the file are encrypted. If necessary, you can also encrypt temporary files. Encrypted file data is not stored in the swap file. All this ensures that the data of the encrypted file does not appear on the disk in decrypted form.
In addition, EFS contains a special mechanism designed to restore access to encrypted files in case the private key is lost. This can happen when deleting a certificate or the user that the certificate belonged to. The mechanism for restoring access to encrypted data is carried out by a special recovery agent, the parameters of which are determined by group policies. In general, the agent's job is to provide a special key that can be used to decrypt the file. Users who have the right to recover data encrypted by other users are defined in group policies.
The Encrypted File System can be used to encrypt files located on other computers. However, the data in this case is transmitted over the network in unencrypted form. If it is necessary to encrypt data and when transmitting over a local network, it is necessary to use specialized protocols (SSL, IPSec, etc.).
To encrypt a file, the following conditions must be met:
- the file must not be compressed (Windows XP independently monitors this condition and, if necessary, unzips the file);
- the user encrypting the file must have a digital certificate that allows him to encrypt files (Windows XP generates a certificate request at the time of encrypting the file).
File encryption process.
The file encryption mechanism is as follows: a folder is created on an NTFS volume that will be encrypted. To encrypt it, open the window Properties for this folder, on the tab Are common press the button Other and select the Encrypt contents to protect data check box. All files placed in this folder will be encrypted, and the folder itself will be marked as encrypted. In fact, only the files in that folder are encrypted, not the folder itself.
Fast symmetric encryption keys are used to actually encrypt the file. A separate symmetric key is used to encrypt each file block. All symmetric keys used to encrypt a file are encrypted with two keys - the user's public key and the recovery agent's public key. In encrypted form, these keys are stored in the fields Data Decryption Field (DDF) and Data Recovery Field (DRF).
For encryption, EFS uses the Microsoft Base Cryptographic Provider. This provider performs encryption using a 56-bit key. Starting with Windows 2000 Service Pack 2, encryption uses a 128-bit key.
The data is decrypted in the reverse order. The content of the DDF field is decrypted with the private key of the user attempting to open the file. If successful, the contents of the file are decrypted using symmetric keys. EFS independently detects the fact of file encryption and searches for the user's private key. If EFS is unable to decrypt the file, the user is presented with a file access error message.
When an administrator deletes a user account, the user loses all encrypted files. To avoid this, create a password recovery diskette in advance, open the window Accounts users and in the Related Tasks section, select Prevent Lost Passwords.
Decryption.
To make the file unencrypted, uncheck the box Encrypt contents to protect data (File Properties -> Others).
Using a recovery agent.
If the file owner's public key is not available, the recovery agent can decrypt the file by using its private key to decrypt the DRF field. If the recovery agent is located on another computer on the network, then the file must be moved to the computer on which it is located in order to be decrypted. private key recovery agent. You can also transfer the agent's private key to the computer containing the files to be recovered. However, copying the private key to another computer is a serious security breach and is therefore strongly discouraged.
On the local computer the default recovery agent is the local administrator. If the computer is joined to a domain, then the domain administrator is the default recovery agent.
Regularly changing recovery agents will provide more high level system security. However, when you change the recovery agent, the old recovery agent loses access to the file and cannot be used to restore it. Therefore, Microsoft recommends that you keep your recovery certificates and private keys until all files that were encrypted using those keys have been updated.
The person designated as a recovery agent has a special certificate containing a private key for recovering encrypted files. The recovery agent does not need to take any special action to gain access to the encrypted file. If his key can be used to decrypt the DRF field, Windows XP will automatically grant him access to the file. When restoring an encrypted file, it is recommended to immediately decrypt it by disabling the Encrypt content to protect data check box in the file properties.
Encrypt files from the command line.
All file encryption and decryption operations can also be performed from the command line using the utility cipher, which has the following syntax:
cipher[.exe] [filename[...]]
cipher[.exe] /K
cipher[.exe] /W:folder
Description of the cipher command keys:
Key | Description |
Without parameters cipher displays information about the encryption of the current folder and all files it contains.
Disable EFS.
An administrator can completely disable the use of file encryption by clearing the Public Key Policy settings. In the operating room Windows system XP file encryption is not possible without a recovery agent, which means an empty recovery policy makes encryption impossible and disables EFS.
 Instructions for using flushing fluid
Instructions for using flushing fluid Why do printheads burn out on Epson printers?
Why do printheads burn out on Epson printers? Installing and configuring the Canon i-SENSYS MF3010 printer Download driver for canon 3010 for scanning
Installing and configuring the Canon i-SENSYS MF3010 printer Download driver for canon 3010 for scanning