What does it mean to encrypt a phone. How to encrypt data on an Android phone
The purpose of this article is to compare three Android encryption apps - LUKS Manager, Cryptonite, and CyberSafe Mobile. It should be noted right away that the comparison will be fair, and not with the aim of highlighting the advantages of a particular program. Each program has its own advantages and disadvantages, in this article they will be fully disclosed.
What is the reason for the choice of applications?
First of all, I would like to note why these applications are involved in the review. With CyberSafe Mobile, I think everything is clear, because you are reading, so it is quite logical to see our program in the review. But the rest of the programs were chosen by the so-called Cauchy method, also known as the scientific poke method, that is, randomly. Of course, when choosing programs, their popularity and ratings were taken into account. So, the Cryptonite program on this moment more than 50 thousand downloads and its rating is 4.3, and the LUKS Manager program has the same rating, but five times less downloads - more than 10 thousand.Many encryption programs have been developed for Android, so we cannot physically consider all of them. Perhaps, in the future, a similar review of other programs will be written and compared with the CyberSafe Mobile program. In the meantime, we will restrict ourselves to the previously mentioned programs.
LUKS Manager
LUKS Manager is one of the first true encryption programs in Android. Before it, the "encryption" programs actually didn’t deal with encryption, but did all sorts of nonsense like assigning a hidden attribute to a file.The LUKS Manager program left an ambivalent impression. I'll start in order - with the installation of the program itself. The program requires you to have root access and have SuperSU and BusyBox installed. Requiring root access is a common feature of all serious Android encryption programs, as there is little that can be done without maximum privileges. But the requirement of SuperSU and BusyBox prompted me to think that the program, in fact, does nothing by itself, and instead of using Android system calls, it uses the BusyBox utilities. In other words, the program is just a shell for system commands. Well, okay, novice users are unlikely to deal with all these commands, so the shell is just what you need - the main thing is that it works.
I already had root access to my device, SuperSU was installed, but BusyBox had to be installed from Play Market... However, after installing BusyBox, the program happily informed me that it did not see it (Fig. 1).

Rice. 1. The LUKS Manager program does not see the installed BusyBox
As a sign of progress, not a revolution
Saving is automatically disabled after connecting to power supply. The changes inside are fully commendable, and new system notifications succeeded. The design changes are pretty superficial, so you use them quickly. Each has some data that we need to encrypt. In today's cloudy time, this is more needed than it used to be. Data is roaming around the world, and we are losing control of it. The only solution is proper encryption. Fortunately, there are a lot of tools.
I will not describe what I did so that the program "saw" it, I will only say that the tablet reboot helped. Somehow it smells like Windows even, not UNIX, which, whatever one may say, is Android. By the way, the bullying took place over the Acer B1 tablet with Android 4.1.2. Not a single tablet was harmed as a result of the experiments :)
After the reboot, the program still started (Fig. 2). The program interface is very simple. I would even say spartan. I crop the screenshots so as not to reduce their size and so that you can see them better.
If you need to encrypt data on your hard drive, flash drive, home archive or files in cloud storage, you can choose either directly in the kernel or in a popular and multi-platform form. However, this procedure has the disadvantage of being in this container. It is static, it takes up one large disk space, and you should measure it up to the required capacity in the future. It is difficult to manipulate and creating such a container from a distance is not fun.
If, on the other hand, there is only silly storage, you will create a half day container. However, unlike other technologies, it does not encrypt the entire block device, but individual files separately. They are then saved one-to-one in their directory, but they have encrypted content and a name.
Rice. 2. LUKS Manager program
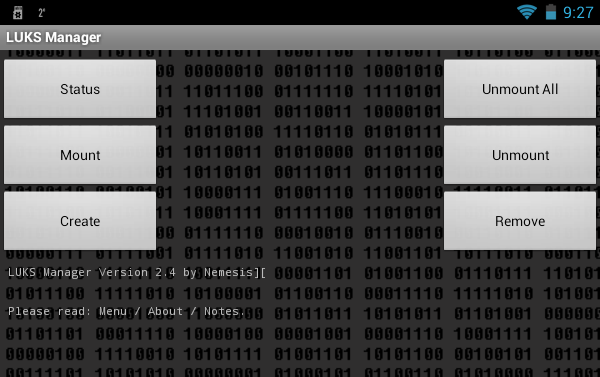
The functionality of the program is also Spartan. You can view which container is mounted (button Status), create a container (button Create), mount (button Mount) and unmount it (button Unmount), unmount all containers ( Unmount all), remove container ( Remove). The fact that the program can create encrypted containers and mount them is good. But nowadays, I would like to see the possibility of cloud encryption, the ability to mount network folders so that you can work with a remote container. I also wanted to see a built-in file manager in case the user does not have such a program installed. After all, for the LUKS Manager to work, I had to root the device, install SuperSu and BusyBox. It turns out that a file manager is also needed. There is basic functionality (displaying files and folders) in the program, was it really difficult to add the functions of copying / moving / deleting files and folders? To access the "explorer" built into the program, press the button to call the program menu and select the command Explore... However, we will talk about this later.
Let's take a look at the program in action. Click the button Create to create a container. The program will offer to select the directory in which the container will be stored (Fig. 3, Fig. 4).
This allows viewers to know the number and size of the files, but it won't help them reveal their names or even the content. Its advantage, of course, is that there is no need to create any container in advance. Encrypted files are stored in one selected directory exactly in the structure that we see in decrypted form. Directories are created, symphonic lines and hard lines are created, individual files are created and deleted.
We'll need two directories to use. One will serve as the real encrypted data store, and the other will be the mount point, the directory in which we will see the unencrypted content. Of course, we should have the right to write both. File names are encoded with a string of initialization vectors. The file holes went through the ciphertext. Now you will need to enter the password for your filesystem.
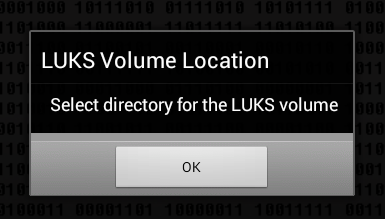
Rice. 3. Click OK
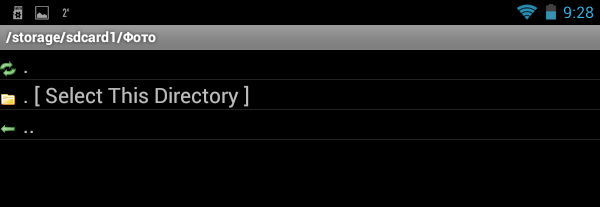
Rice. 4. Select a directory and click Select This Directory
Next, you need to enter the name of the container (Fig. 5), the password for access (Fig. 6) to it and the size of the container (Fig. 7). The program does not display the entered password and does not offer to confirm the password, so there is a possibility of an error when entering the password - then it will not work to mount the created container and this must be taken into account when working with the program.
You will need to remember this password as there is absolutely no recovery mechanism. It wasn't hard, just hit enter and enter your password twice. You can, of course, go into expert mode and select many options from the key length ciphers used so that the filenames are encrypted.
So we can start using it, but we'll stay with the file for a while. It contains the selected options for our encrypted volume and, above all, the encryption key, which is itself encrypted with the password you chose. For example, this allows us to easily change the password, but at the same time it means that if we come to this file, we will no longer be able to decrypt individual files.
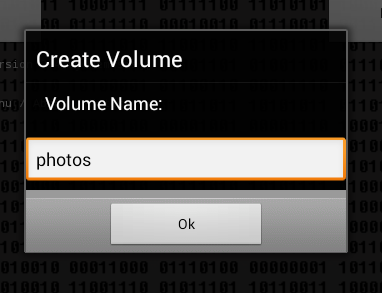
Rice. 5. Container name

Rice. 6. Password for access to the container

Rice. 7. Container size
The next question is how to format the container: as FAT (will be compatible with FreeeOTFE) or as ext2 (Fig. 8). LUKS Manager creates containers compatible with the Windows program. As for me, it would be better if the program had support for TrueCrypt. However, it should be noted that finally FreeOTFE has support for 64-bit Windows versions, which allows you to more fully use the LUKS Manager + FreeOTFE bundle on modern computers... It would be nice if LUKS Manager had the ability to remotely mount a container that resides on a Windows machine. Then you could create a container on a PC using FreeOTFE and remotely mount it on your Android device. The advantage of such a solution is that there is no need to clutter up the device's memory, and the data itself would not be physically stored on an Android device, which is much more likely to be lost than a regular PC.
Correct paranoia can save the file separately and thus completely avoid attempts to decrypt the data itself. You see an encrypted representation of our secret data. The files themselves are eight bytes in size because an eight-byte initialization vector is stored at the beginning of each file for added security.
When it stops speaking, just call the following command and safely unplug the volume and lock it. It basically allows you to change the password to existing volume, but it also has other options. Another command verifies that all files in the encrypted space are decrypted using a key in the control file. Interestingly, this file is not ignored by the program and is listed as erroneous.

Rice. 8. How to format the container?
Next, the program will inform you that the container has been created and mounted to the / mnt / sdcard / folder<название контейнера>, in our case it is / mnt / sdcard / photos (fig. 9). In the program settings, you can change the name of this folder.
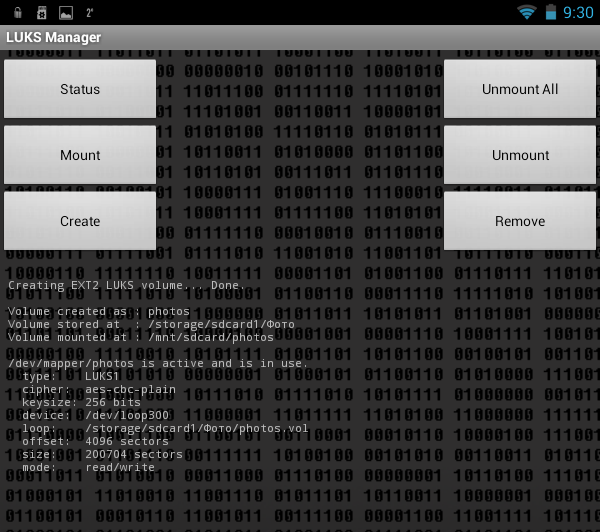
Rice. 9. The container is mounted
The decode and encode commands let you decrypt or encrypt the specified filenames. This is useful if you are looking for information in debug output that only displays filenames in encrypted form. You can use the reverse procedure when you only want certain files from the backup and you need to know what they are called encrypted.
After running this command, you will of course ask for a password, and then the program waits for the file name to be entered. The following example shows both options. This allows you to connect or disconnect the encrypted volume with a single click, and you don't have to work with the line at all.
It remains to launch some third-party file manager and copy the files to the created container (Fig. 10).
Rice. 10. Files copied
We try to unmount the container (button Unmount), while the program displays a window allowing you to select which container you want to unmount (Fig. 11).
Usage on other platforms
It is saved in the notification area and, when clicked, shows a menu where you can enable and disable individual volumes. It works very accurately, allowing you to simply create, edit, or attach an encrypted volume. Try to share your experience in the discussion. Some users need similar cryptographic technologies to work on other platforms. Especially when used in cloud storage, you need to access files from different platforms.
If you use any of these services, you can always get the data. It is much easier to combine encrypted and unencrypted parts on different media. In addition, it can take advantage of the properties of the file system, making it difficult to create hard links as well as symbolic links or permissions.
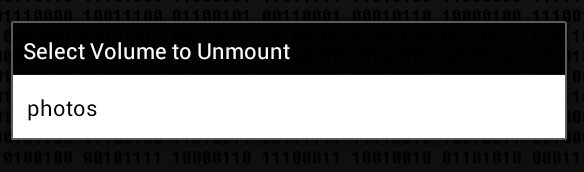
Rice. 11. Unmounting the container
After that, launch the file manager and go to / mnt / sdcard /. The photos folder exists and for some reason it has not been deleted, but access to it is denied (Fig. 12). Typically such temporary folders should be removed after unmounting. But these are trifles, in principle.
They are just files like any other. They are simply not readable to the user. Backups are automatically encrypted, and an unauthorized person does not read anything. Of course, the user can store photos, videos, music or parts of applications on the card, but the bulk of the application's work always remains in the phone's memory.
During the process, you will be able to choose whether to use the entire storage memory as the internal storage of the phone or only a part of it. However, we strongly recommend using the entire memory card. The security of mobile data is an important issue as users are exposed to both the loss and theft of their smartphones. According to these guidelines, users should not be exposed to performance degradation.
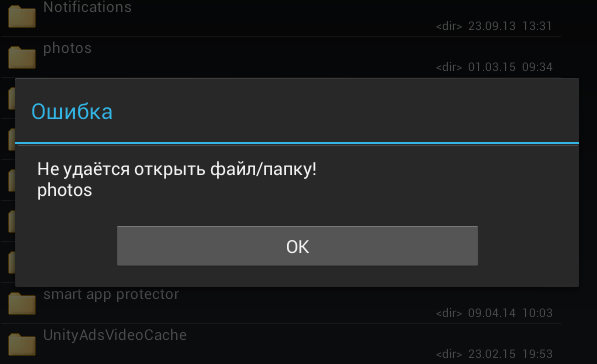
Rice. 12. Access to / mnt / sdcard / photos is denied
Now let's see what the program has in the settings. Press the menu button and select the command Preferences(fig. 13). Here's what we see useful (Fig. 14):
- Encryption keysize- encryption key size, by default 256 bits.
- Mount directory- the folder to which the containers will be mounted.
- Explore on mount- if this parameter is enabled, after mounting the container, its contents will be displayed in the built-in "explorer" (Fig. 15). However, the built-in file manager only allows you to view the contents of the container, it does not allow you to manage files. The maximum that is useful in it is a window with information about the file, which appears if you click on the file in the container and hold your finger for a while (Fig. 16).
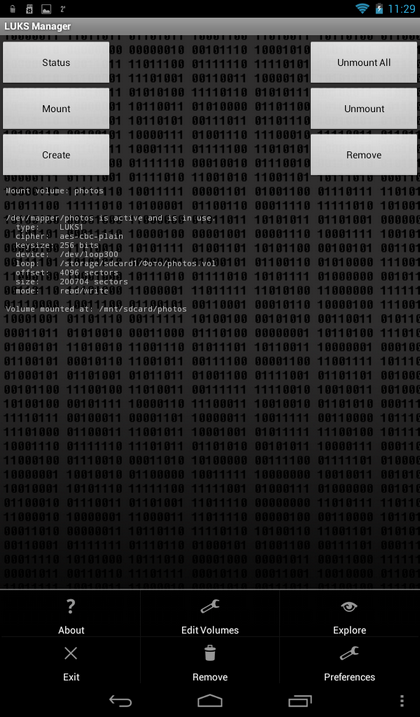
Rice. 13. Program menu
The question of such protection of data stored on mobile device, was hotly debated last year. This is not required for slower hardware, so users have the confidence that better protection will not compromise comfort with slightly cheaper devices.
This can help speed up the process, which greatly speeds up encryption at the file system level. For example, encryption is not required for devices that do not have a secure lock screen. Such a requirement may discourage users who may prefer more simple methods, or simply cannot provide any gesture of transfer. In this case, the default password is used, which makes the situation amusing: on the one hand, the data will be encrypted, on the other, if the device is stolen without a locked screen and thus will not provide any security.
![]()
Rice. 14. Program settings

Rice. 15. Built-in file manager
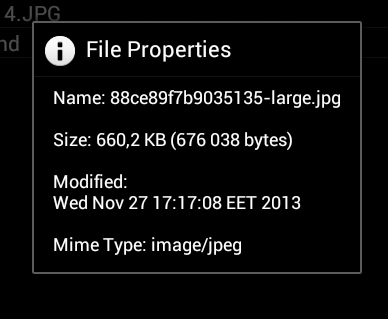
Rice. 16. Window with information about the file
While the results are counterintuitive in some places, setting a certain encryption rate limit seems like a good idea: we don't have to worry about new devices being too slow despite theoretically good components. No hardware encryption support and fast enough internal memory a smartphone or tablet can slow down significantly. Of course, this situation probably will not attract representatives of various government organizations.
The current version with number 0 implies, in particular, encryption by default of all data stored on the device. The importance of safety does not need to be reminded to anyone. If we lose our phone or are stolen, then the thief will have to work harder to access the stored files.
Now let's summarize. The advantages of the LUKS Manager program include:
- The program is free, but requires a paid BusyBox (however, there is also a limited free version)
- Encryption is performed "on the fly"
- Working with a mounted container is carried out as with a regular folder. It's pretty simple.
But the program has many shortcomings:
Encryption for mobile devices cannot be too strong or too weak. Therefore, it was decided to check how the same OS on one device if one of them finishes working with data encryption and the other device turns off this feature.
But now it turns out that encryption is optional. Unfortunately, this series of processors is just entering the market, so manufacturers now have to decide whether to enable encryption at the factory and expose a significant reduction in test results, or maintain performance, but at the expense of encryption. Unsurprisingly, most of them solve the second solution.
- In addition to the program, you must install additional applications SuperSU and BusyBox (which, by the way, is not free, although LUKS Manager itself is free).
- Limited functionality of the program: no ability to mount remote containers, no cloud encryption, no support for mounting network folders.
- Inconvenient built-in file manager that only allows you to view files and folders.
- There is no way to choose an external file manager.
- The folders to which the container is mounted are not automatically deleted after the container is unmounted.
- There is no support for the Russian language.
Cryptonite
The Cryptonite program is quite young and in the testing stage, so it can hardly be used to encrypt any particularly sensitive data. To be fair, it should be noted that the developers honestly warn about this when the program is first launched (Fig. 17).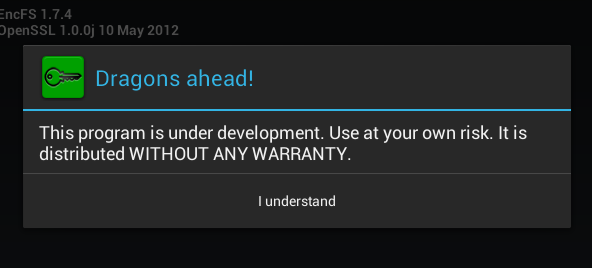
Rice. 17. First launch of Cryptonite
Research and analysis, Kaspersky Lab. His statement is quoted in full. When it comes to encrypting the entire device, we need to keep in mind that unless we provide the crypto key in the form of a strong password, token, or something similar, we are dealing with a dangerous placebo. If the encryption key is embedded in the product, encryption is practically useless and only provides a false sense of security and the next point on the list of device features. When an attacker has access to the key, even military-grade encryption won't protect our data.
Concerning system requirements, then the program needs root access and a kernel with FUSE support (Filesystem in Userspace, File system in user space). The requirement to support FUSE can be safely attributed to the shortcomings of the program, since not all devices support FUSE. Reinstall any additional programs not necessary (except for file manager).
The functionality of the program is already somewhat better than that of LUKS Manager. She knows how to create not only local containers, but also encrypt your files on DropBox. DropBox support automatically means cloud encryption support, so this program already stands a cut above LUKS Manager.
In fig. 18 shows the Cryptonite program after closing the annoying message that you are using an experimental version of the program. Tab Dropbox allows you to encrypt files on your Dropbox, tab Local used to create a local container, and in the tab Expert an ordinary user has nothing to do.
This problem is especially evident for smartphones, as they cannot be used with external tokens, and using long secure passwords is simply inconvenient. Humanity has come up with many ways to keep the secret. To send a private letter to ancient Rome, an aristocrat could shave a slave's head, write the content of information on his skin, wait until the hair grows out and sends it to the addressee. Fortunately, computers that were originally built to break military ciphers now offer the ability to keep their secrets for themselves - by properly encrypting them.
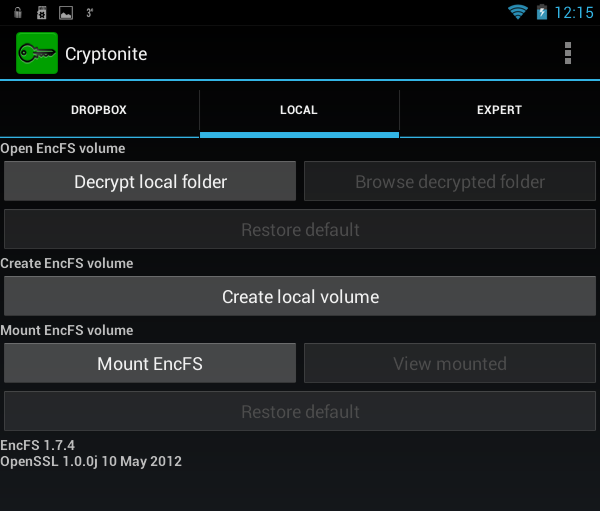
Rice. 18. Cryptonite program
To create a local container, click the button Create local volume, after which you will again see a warning that this function experimental (Fig. 19). Then, as usual, you need to select the encryption method (Fig. 20), the location of the container, enter the password and its confirmation (Fig. 21). I liked that the program prompts you to enter a password confirmation, which eliminates the wrong password when creating a container.
For a long time this feature was reserved exclusively for governments, but today it can already be used by anyone. More importantly, even if you have never thought about it, you will always have a secret cipher. When it comes to encryption and protection, the reaction of people at the first moment is often like this: "I have no secrets - nothing to hide." They usually mean, "I don't think anyone would be interested in digging my computer or smartphone for something of value."
However, it turns out that these are only hopeless hopes. There may be nothing cryptic about the content you store, but you don't necessarily want to share it with others. Are you sure you want to explain to your wife that Katarzyna is a colleague from another department at work, and the “meeting tomorrow” you are going to meet is really a business meeting with dozens of other people?
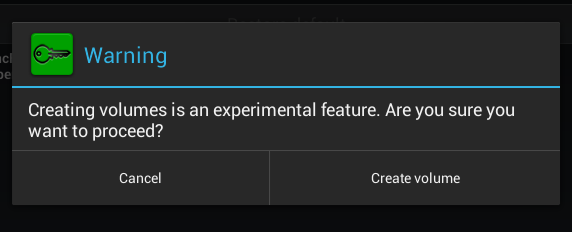
Rice. 19. Again annoying warning
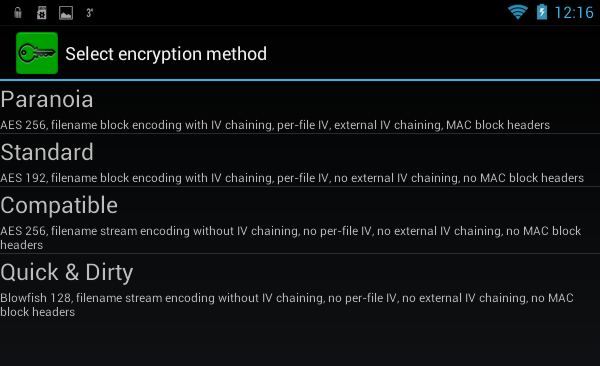
Rice. 20. Choice of encryption method
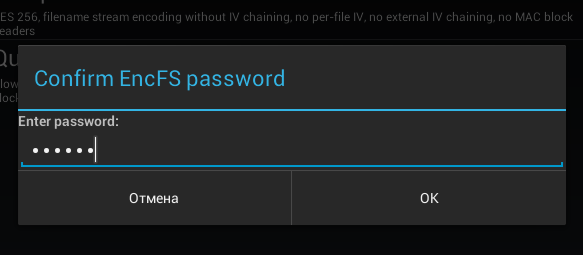
Rice. 21. Entering password confirmation
You can mount the created container with the command Mount encfs in the tab Local... The program will prompt you to select a container. After entering the password, the container will be mounted to the /mnt/sdcard/csh.cryptonite/mnt directory (Fig. 22). The directory for mounting is specified in the program settings (Fig. 23).
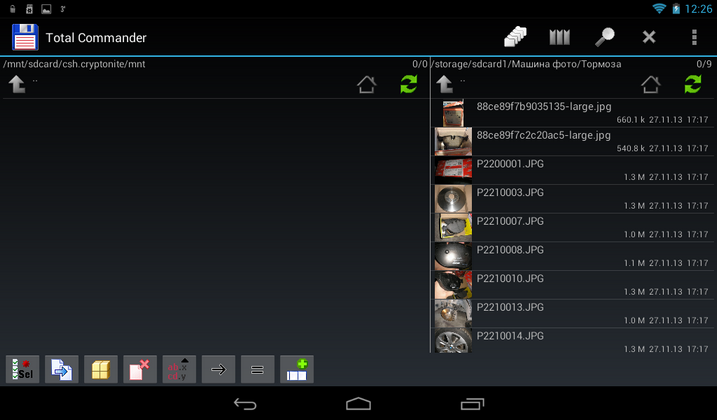
Rice. 22. The container is mounted
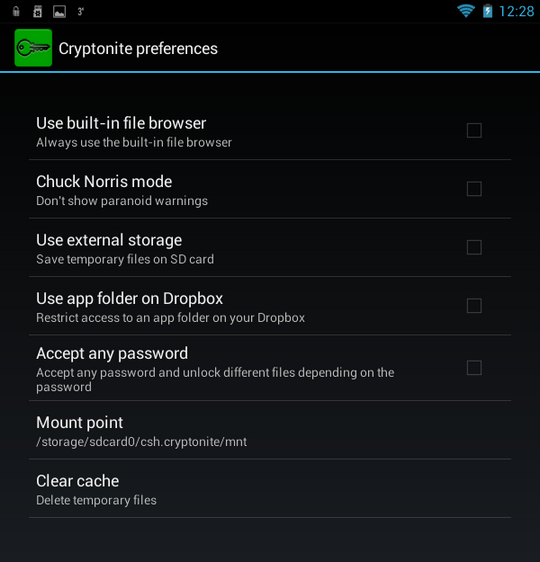
Rice. 23. Program settings
There is nothing particularly interesting in the settings, except for the mount folder ( Mount point), as well as the Chuck Norris mode, which allows you to turn off annoying and meaningless warnings. You can also enable the use of the built-in file manager when mounting a container ( Use built-in file browser), but given the traditionally meager functionality of this part of the program (Fig. 24), I do not recommend enabling this parameter. This "file manager" cannot even open the file. It only allows you to view the contents of the container and nothing else.
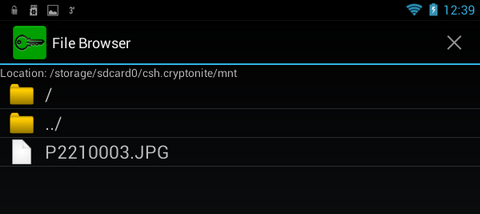
Rice. 24. Built-in container viewer
Benefits of the program:
- Cloud encryption support (Dropbox).
- Encryption on the fly.
- Support for TrueCrypt containers, which is useful if you need to work with the container on a stationary PC.
Disadvantages:
- Requires FUSE support, which not every device has.
- A very meager file manager that only allows you to view the contents of the container and nothing else
- No support for network folders (although this drawback is slightly mitigated by support for Dropbox)
- The program is still experimental (although it appeared quite a long time ago, and since then it has been downloaded by more than 50,000 people). It's up to you to decide whether to use it or not, but I wouldn't use it to protect sensitive data. Better to look for another program.
- There is no support for the Russian language.
CyberSafe Mobile
We have already reviewed CyberSafe Mobile several times in our blog, so there will be no detailed description of it. I strongly recommend that you read the article, which describes one of the use cases of the program.Therefore, instead of a review of the program, so as not to repeat itself, it will be compared with the programs previously described in this article.
First of all, it should be noted that to work with the program you do not need root rights... Yes, in this case, the functionality of the program will be limited, and you will not be able to mount the created safe (as CyberSafe Mobile calls an encrypted container), but your smartphone will not “fly off” the guarantee if you get root access. However, given that the program has a full-fledged file manager, this is not a problem. You can work with files in the safe without mounting it and installing a third-party file manager. For security reasons, the program does not allow taking some screenshots, so the window of the built-in file manager, which displays the contents of the safe, was only able to be photographed with an ordinary camera (Fig. 25). As you can see, the program has a full-fledged file manager. Even if this is not ES Explorer, but, unlike the previously described programs, the built-in file manager Cybersafe Mobile can manage files - copy, move, delete, create new files and folders. I apologize for the quality of the picture, but so that there was no glare, the tablet was photographed without a flash, so the photo is a little dark.

Rice. 25. Built-in file manager CyberSafe
In the program mount settings, you can select (Fig. 26):
- Mount method- as already noted, if your device does not have root access or does not support FUSE, then you can not mount the safe, but work with it through the built-in file manager.
- Base path for mount- the directory to which the safes will be mounted.
- Third party file manager- the program allows you to use both the built-in and an external file manager, and it detects the managers already installed on your device and allows you to choose one of them.
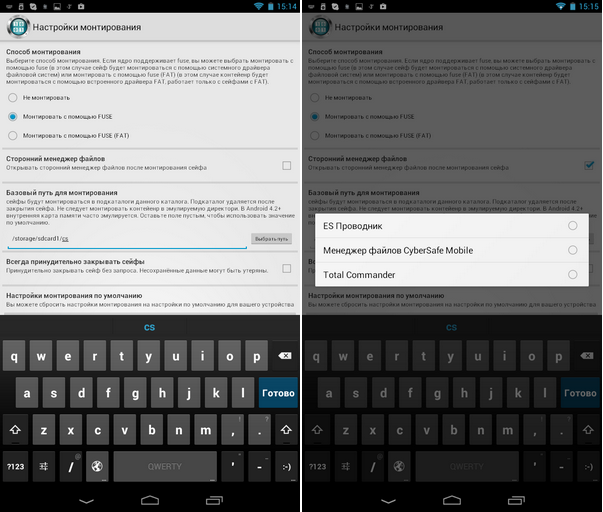
Rice. 26. Mount options
It is also worth noting the Russian-language interface of the CyberSafe Mobile program, which makes it easier to work with the program for users who do not own English language(fig. 27).
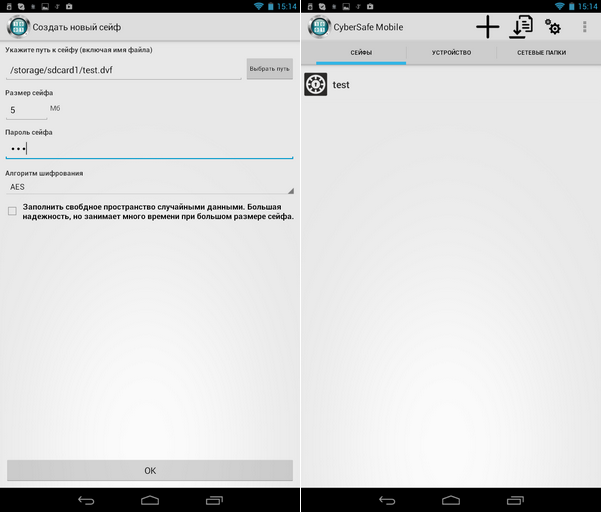
Rice. 27. Program interface. Safe creation
Only thanks to all this (the ability to work without root and FUSE, a full-fledged file manager and a Russian-language interface) the program is head and shoulders above LUKS Manager and Cryptonite. But that is not all. The program has a number of functions that lead to the knockout of competitors.
Firstly, it supports the GOST algorithm - unlike other programs that use only AES or Blowfish (Fig. 28).
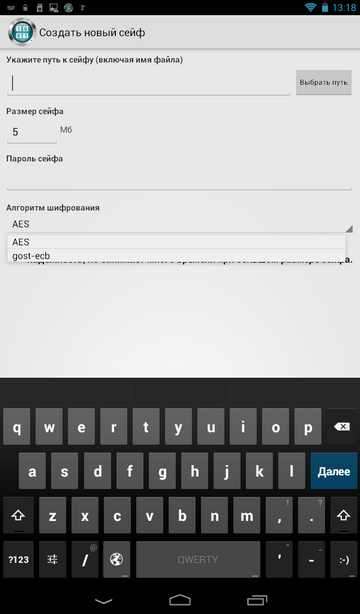
Rice. 28. Choosing an encryption algorithm when creating a safe
Secondly, the program supports mounting network folders, which allows the use of a remote safe located on a remote PC (Fig. 29). The principle is simple: the container itself is stored on a PC and shared over the network. It turns out that the container is opened on a smartphone, it is always stored on a PC in an encrypted form, data is also transmitted over the network encrypted, which excludes their interception. All actions to encrypt and decrypt data are carried out on a mobile device. Even if you lose your device, no one can even access the encrypted data, since it is stored on remote computer.
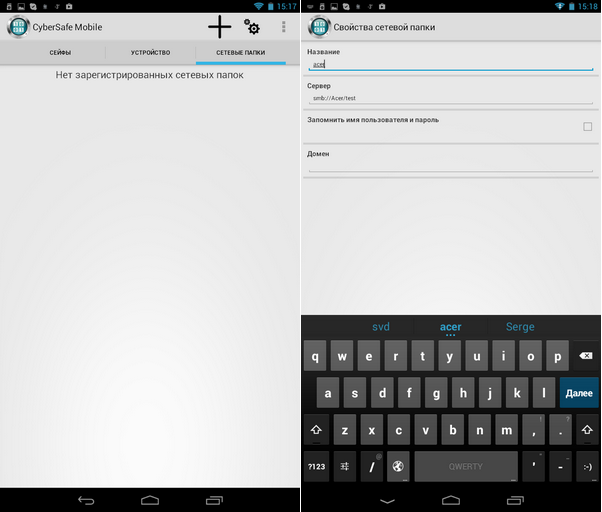
Rice. 29. Working with network folders
You can create a safe both with the CyberSafe Mobile program and with the desktop version of the program - CyberSafe Top Secret. It should be noted that CyberSafe Top Secret is not needed to fully work with the safe - you can create a safe on your mobile device and copy it to your PC. In other words, you do not need to buy CyberSafe Top Secret software to use the safe on your smartphone remotely. But if you need to organize, then of course you need CyberSafe Top Secret software.
When installing free software URSafe Media Redirector can automatically redirect the photos you create (and other files, such as documents) to a safe, which is physically located on the remote computer. You can read more about this in the article. And the article shows how to store containers on a remote server, not on a PC connected to your local wireless network.
Everything has disadvantages. However, CyberSafe Mobile practically does not have them. The disadvantages include the need to support FUSE, but this drawback is leveled by the fact that the created safes can be opened without mounting, but only in the built-in file manager. It should also be noted that the program is paid, but its price is not high for a program of this class (do not forget what functionality the program has and do not forget that it supports, in addition to the AES algorithm, GOST). Well, I don't really like the impossibility of creating some screenshots of the program, but it's better from a security point of view :)
Now let's summarize. CyberSafe Mobile advantages:
- Ability to work without root access and FUSE support (just safes will not be mounted).
- Transparent encryption on the fly
- Own full-fledged file manager
- Russian language interface
- GOST encryption algorithm support
- Ability to select a third-party file manager in which the contents of the safe will be opened
- Support for mounting network folders
- Ability to work with remote containers (VPN-safe)
- The ability to share the same container on a smartphone and on a PC (using the CyberSafe Top Secret program).
- No need to install (buy) third party applications(as is the case with LUKS Manager)
Disadvantages:
- The program is not free, but there is a Lite version of it that does not support mounting and network folders... If you do not plan to use remote safes, and your device does not support FUSE, or you do not want to get root access so as not to "fly off" the warranty, then the Lite version is just what you need. CyberSafe Mobile will be free for you, and the functionality of the Lite version will be even better than that of the free LUKS Manager, taking into account a full-fledged file manager.
- For the program to work properly, FUSE support is needed (however, this is no longer a problem on modern devices).
As you can see, the program does not have such shortcomings, and their allocation is more of my nitpicking to the program, so that no one accused me of bias. I think no one had any doubts that the winner of our comparison today was the CyberSafe Mobile program. If you still have questions, we will be happy to answer them in the comments to this article.
Tags: Add Tags
You use your Android smartphone (tablet) to save personal photos, read important emails shopping online with your credit card, editing and transferring important documents? If your answer is yes, then you should consider encrypting your device.
Unlike the iPhone, Android devices They do not automatically encrypt the data that is stored on them, even if you use a password to unlock the device, but if you are using Android Gingerbread 2.3.4 or higher, then encryption is easy to enable.
Encrypting your phone means that if your phone is locked, your files are encrypted. Any files sent to and received from your phone will not be encrypted unless you use additional methods.
The only difference between an unencrypted and an encrypted phone from the user's point of view is that you will now have to use a password to unlock the phone (tablet).
If your phone is not encrypted then the password is just a screen lock. In fact, in this case, the password simply locks the screen - that is, it does nothing to protect the files that are stored on the device. So, if attackers find a way to bypass the lock screen, then they get full access to your files.
In case the phone is encrypted, the password is the key that decrypts the encrypted files.
That is, when the phone is locked, all data is encrypted, and even if attackers find a way to bypass the lock screen, all they find is encrypted data.
How do I enable encryption on an Android device?
1. Open the Settings menu.
2. In Settings, select Security> Encryption (Encrypt device).
3. In accordance with the requirements, you need to enter a password of at least six characters, according to at least one of which is a number.
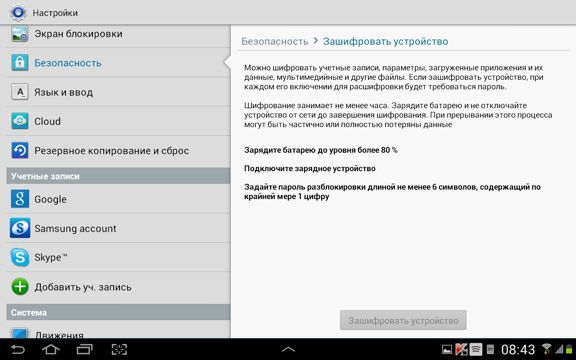
As soon as you set the password, the process of encrypting your files will start. Encryption can take an hour or more, so you must turn on the charger before encrypting it.
Once the encryption process is complete, you're done! Make sure to save your password in a safe place as it will come in handy every time you want to access your phone. Please note that if you forget your password, there is currently no way to recover it.
In fact, encrypting Android devices, along with the obvious advantages, also has significant disadvantages:
- Imagine that every time you want to call, you need to type a complex password. I wonder how soon you get tired of this?
- You will not be able to decrypt an encrypted device, it is simply not provided. There is only one way to decrypt - reset the phone to factory settings. In this case, of course, all your data will be lost. It will look especially interesting if you forget to make a backup beforehand.
Thus, today there is a difficult choice - either you encrypt your device and put up with huge inconveniences, or you get usability, but at the expense of security. Which path will you choose? I do not know. Which path would I choose? I can't answer either. I just do not know.
Vladimir BEZMALY , MVP Consumer Security, Microsoft Security Trusted Advisor
 Architecture of a distributed control system based on a reconfigurable multi-pipeline computing environment L-Net "transparent" distributed file systems
Architecture of a distributed control system based on a reconfigurable multi-pipeline computing environment L-Net "transparent" distributed file systems Email sending page Fill relay_recipients file with addresses from Active Directory
Email sending page Fill relay_recipients file with addresses from Active Directory Missing language bar in Windows - what to do?
Missing language bar in Windows - what to do?